Control-M SSL Configuration
Control-M works with the Secure Sockets Layer (SSL) and Transport Layer Security (TLS) protocols, ensuring secure communication between the various Control-M components.
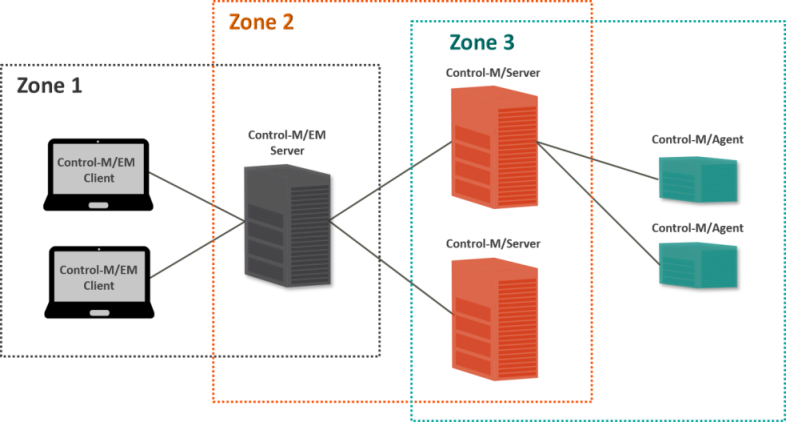
SSL for Control-M authenticates and secures communications between one or more of the following:
-
Control-M Web Server and its clients (see Zone 1 SSL Configuration)
-
Control-M/EM Server and Control-M/Servers (see Zone 2 and 3 SSL Configuration)
-
Control-M/Server and Control-M/Agents (see Zone 2 and 3 SSL Configuration)
-
Control-M/EM and the LDAP Server (see LDAP SSL Configuration)
Depending on your setup, you can enable security for the following components:
-
Control-M Self Service (see Zone 1 SSL Configuration)
-
Control-M Workload Change Manager (WCM) (see Zone 1 SSL Configuration)
-
Control-M MFT (see Configuring Control-M MFT for an Alternative CA)
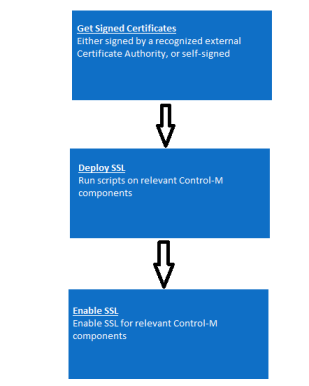
To configure SSL in your environment, you must do the following:
-
Get Signed Certificates: Signed certificates are required for enabling secured communication using SSL protocols. Control-M components supports only PEM certificates, which are ASCII-encoded X.509 certificates. BMC recommends that you replace the existing certificates by bringing your own certificates, signed by a recognized Certificate Authority (CA). You can either get the signed certificates from your security administrator, or bring your own, as follows:
-
Get Certificates from Your Security Administrator: Obtain a pkcs12 keystore, or the private key, the signed certificate, and the certificate of the root CA in *.pem file format. The last file must also contain the certificate chain from the certificate that signed your certificate to the root CA certificate, if required.
-
Get Certificates with a CSR File: Obtain a signed certificate from a recognized CA using a Certificate Signing Request file. If the server certificate was issued by an intermediate CA, which has a certificate trusted by a root CA, whether directly or by a chain, you must obtain the certificate chain from the CA.
BMC recommends that you replace the existing certificates by bringing your own certificate (signed by a recognized CA).
For demonstration or proof-of-concept purposes, you can use the default certificates that come with the component or generate new certificates from the CCM, which creates a CA that is signed by BMC for the specific environment. For more information, see Generating Self-Signed Certificates.
-
-
Deploy SSL: To create an SSL policy, you must deploy the keystore, which contains the private key, the signed certificate, and the certificate chain to the relevant Control-M components.
-
Enable SSL: Enable SSL for relevant Control-M components.
The following diagram shows the multiple ways you can configure SSL in environment based on zones:
 YouTube
YouTube Twitter
Twitter Facebook
Facebook LinkedIn
LinkedIn